Can we take your fingerprints, please?
Ad scammers are constantly looking for more ways to lure users into their traps. In that respect, they’re not that different from advertisers – the more traffic they lead into the top of the funnel, the more wins they get at the bottom. The same is true for the quality of the traffic – better quality leads yield higher conversion rates.
Like advertisers, scammers give a lot of thought to defining their target audience and determining the most effective channels to reach it. But the similarities end there. Because, unlike advertisers, scammers need to drive quality traffic to their funnels without being detected by ad quality and security systems like GeoEdge.
That’s why scammers stay in the shadows, hidden behind cloaking mechanisms that let them reveal a different face of their campaign each time their ads are clicked, depending on the client or user.
Cloaked attacks are expressly designed to pass through scans at the ad tag level, before the impression is rendered, and to show scanning tech a false result.
The common thread is that cloaked attacks can distinguish between environments in which there is an end-user and testing enviornments in which there isn’t. “Non-user” testing environments are mostly search engines and ad monitoring tools. Cloaking relies on detection processes that analyze various parameters, including IP address, browser, device, and more to identify artificial, non-user environments.
Cloakers typically bypass layers of manual and automated quality assurance by hiding their real URLs within lines of code, or including code that looks like the URL of a legitimate publisher or company. The fake or obfuscated code looks legit to basic scanning tools, which allows it to reach its intended destination where users interact with it directly.
Below is an example of a financial scam campaign hidden behind a cloaking mechanism.
Image 1
Image 2
Cloaking in action: Two faces of the same campaign, a dummy advertorial blog post (image 1), and a deceptive fake news site (image 2).
To decide which face to expose to which user, scammers run tests and checks in real-time. These checks tell them whether the user is a real, live human they can try to scam, or whether it’s an agent of a detection system designed to track them down and block their scams from reaching users.
The testing stage is carried out in two steps – first, the scammers try to collect as many device-identifying data points as possible to build a unique fingerprint of the client. Then, they run vetting logic that determines whether the user is exposed to the scam or shown a dummy landing page.
Fingerprinting techniques take many forms and utilize many different techniques. Here are some of the most common fingerprinting techniques out there:
Basic fingerprinting techniques
At the root of scammers’ attempts to distinguish detection machines from real users lies the assumption that ad scanning systems run virtual machines hosted by desktop machines. These virtual machines are set to act like different devices each time. A machine can present itself as an iOS mobile device when it’s actually a desktop Windows machine emulating an iOS device.
If this is the case, the machine’s real identity can be detected by checking device-related characteristics and comparing them against those of the emulated device type. If the results don’t match, the scammers know the client is not a real user and redirect it to a dummy landing page, avoiding exposing their scam.
Basic fingerprinting techniques verify the client’s identity by testing the device’s functionality.
The example below shows an attempt at trying to create a touch event, thus checking whether the device has touch functionality.
If the device claims to be a mobile device but lacks touch functionality, the scammers can tell the client is actually a testing environment.
Here is an attempt to identify the browser by querying the navigator interface, which represents the state and the identity of the user agent.
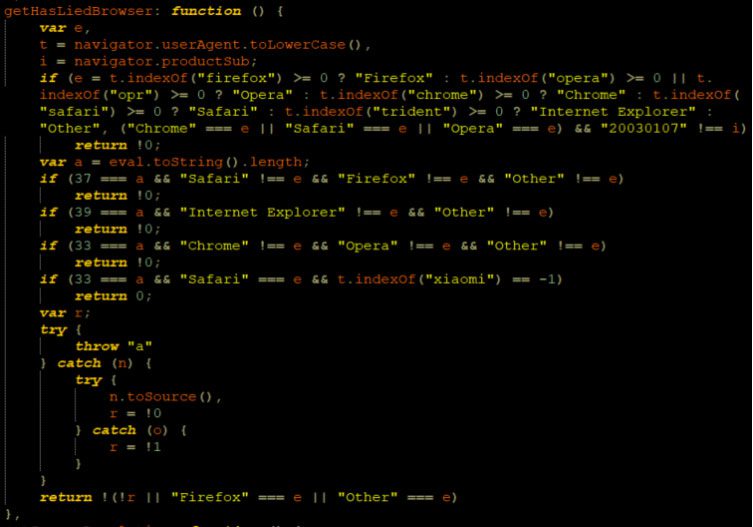
Changing the user agent on the HTTP requests is easy in a testing environment, but changing it on the browser level is much more complicated. Scammers know that, and they assume that by querying the navigator interface, they’ll be able to expose differences between it and the HTTP calls.
In a similar example, scammers try to verify the OS on which the client is running:

Another common test checks the browser for screen resolution / window size:

A window size of 1055*1920 clearly can’t be returned for a mobile client. That can point scammers to the machine’s true identity.
We’ve also seen scammers testing the battery level, assuming a human user typically won’t have 100% battery, while machines that are always connected usually have a full battery at all times.
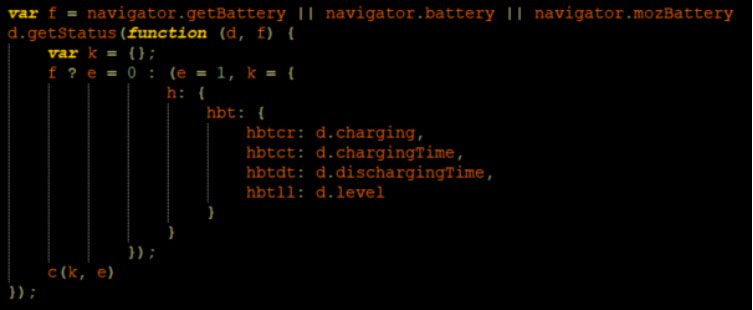
Finally, once all data points have been collected, a scammer can run the vetting logic on the client-side and decide on the next step:
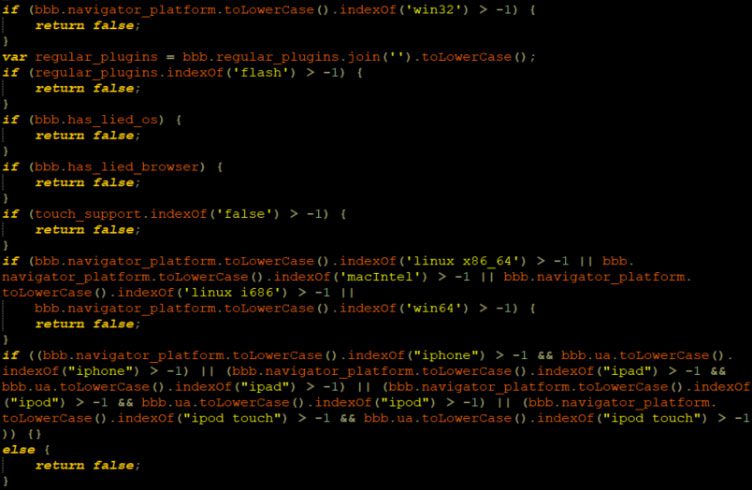
Only a client that has returned ‘True’ for the vetting process is then exposed to the scam.
There are two options for the next step:
Scammers who rely on automatic redirects to drive traffic to their scams use the fingerprinting process to vet which users to automatically redirect to the scam LP. Scammers who rely on clickbait ads to drive traffic to their scams will use fingerprinting to vet which users to redirect through cloaking after clicking the ads to the next step, which is often a deceptive landing page designed to mislead users into “buying” a malicious offer.
Advanced Fingerprinting Techniques
Canvas fingerprinting
Canvas is an HTML5 API that uses JavaScript to draw graphics and animations on a web page.
Scammers use canvas as an additional data point to calculate a client’s unique fingerprint.
They rely on the fact that a specific canvas image may be rendered differently on different devices. There are several reasons for this. Web browsers use different image processing engines, image export options, and compression levels, so the final images may yield different checksums even if they are identical, pixel for pixel. Operating systems also have different fonts. They use different algorithms and settings for anti-aliasing and sub-pixel rendering.
In this example, you can see the scammers creating a canvas element and checking for the ‘vendor’ and ‘renderer’ canvas objects to identify the graphic card of the device.

Canvas fingerprinting can identify operating systems, browsers, and devices by version and yield a signature with a uniqueness of 99.5%+. Scammers use this as additional fingerprinting to reach higher identification accuracy before executing vetting logic.
WebGL Fingerprinting
WebGL is a JavaScript API designed to render 3D graphics in the web browser without the use of a plug-in. WebGL apps usually have a control JavaScript code and a special effects code that the computer’s GPU executes.
Browsers can be queried for a WebGL report that checks the WebGL support of the browser, produces WebGL device fingerprinting, and shows additional WebGL and GPU capabilities related to the browser’s identity.
There are two kinds of WebGL fingerprints:
- WebGL Report Hash: A hash calculated from the WebGL Browser Report, which lists all WebGL capabilities and supported extensions
WebGL Image Hash: A hash calculated from the array of pixels created by drawing a WebGL gradient shader like this one:

Obtaining these hash results requires only the WebGL API. It doesn’t depend on browser differences, so the fingerprint will be similar across all browsers on a single device, allowing the scammers to identify the device itself on a very accurate level.
Once again, scammers add these results to their overall checks to add another layer of accuracy in their attempt to fingerprint and identify the true identity of the user.
Detecting the detection
While fingerprinting works in favor of scammers, helping them pick up on machines and scanners, it also works against them. When we at GeoEdge see an advertiser trying to fingerprint users at such an advanced level, we take it as a sign that their intentions are most likely malicious.
When we detect ads with such fingerprinting attempts, our system regards them as suspicious. Even though scammers may try to hide and distort their fingerprinting code, we have the means to detect them in real time and flag them as highly suspicious for further analysis by our security researchers.











