What comes to mind when you think of a silent threat? Cyber attacks are among the most feared silent threats, as they don’t come with any obvious warning signs. Exploit Kits are a perfect example of silent but deadly cyber threats.
What Are They?
Exploit Kits are a type of toolkit cyber criminals use to attack vulnerabilities in systems to distribute malware and perform a number of malicious activities. These digital threats silently exploit vulnerabilities on users devices while browsing the web.
How Do They Work?
The attackers behind Exploit Kits deceive users by running ads on various networks, which leads the users to malicious pages that end up using known vulnerabilities for IE browsers. When vulnerabilities are identified, cybercriminals tap into them and inject malware into the user’s machine.
Who Do They Target?
These Exploit Kits primarily target windows users using Internet Explorer versions 8 through 11. The reason being, these browsers are the easiest to hack due to lack of automatic updates.
It’s important to mention that users using different browsers, including Chrome, Firefox, updated Internet Explorer, will not be attacked by Exploit Kits thanks to the ramped-up security which has already addressed security vulnerabilities.
Tracking Down Cyber Criminals
GeoEdge’s fierce security team searches for these relentless attackers day and night.
The team profiles them and alerts customers to new threats that may appear to their users via the traffic they drive to their networks.
The security team has uncovered the latest Exploit Kit running on various networks, and has provided a rundown of the scam!
Let’s get started!
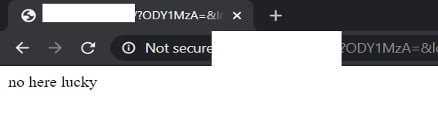
First, we can see the landing page that ‘filters’ vulnerable users (I.e. vulnerable browser)
Here you can see the pcap of redirects from the landing page:

The landing page itself does ‘server side filtering’ and sometimes the developer adds a few funny comments.
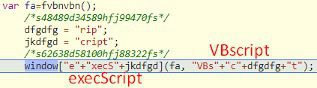
This is the code from the Exploit Kit, we can see here how the attacker runs the malicious VBscript code:
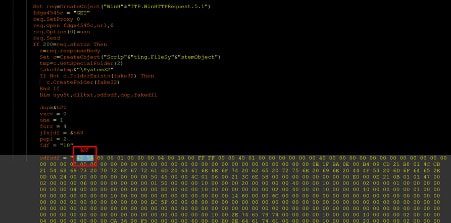
And this is the actual vbscript with the payload:
Exploit Kits are a fast growing online threat that cybercriminals seem to favor as of lately to execute web-based attacks! We hope you now have a better idea of what an Exploit Kit does and how it works!
Need a bit more info on blocking malicious attacks?