As the price of bitcoin reached a record high of $41,000 this past weekend, GeoEdge has uncovered the Hermexx global malvertising campaign which baits and defrauds users employing deceptive Bitcoin ads.
While GeoEdge’s security researchers identified 5 new flavors of cloakers, this research will explore the anatomy of the attack through the channel of one individual cloaker.
Anatomy of the Hermexx Attack
The Hermexx cloaker, named after the Greek god of commerce and theft, has successfully seized the opportunity to exploit bitcoin’s recent rally and deceive users primarily in the UK, Germany and South Africa. Moreover, utilizing deceptive cryptocurrency lures, the cloaker has targeted Andriod users through Google Chrome.
The sophistication of the campaign included fingerprinting the user’s device itself, then fingerprinting the environment by requesting the time zone of the device and comparing the time zone of the IP.
Utilizing GeoEdge’s patented behavioral code analysis technology and advanced malware detection including our unique machine learning algorithm comprised of a dozen mechanisms including de-obfuscation, and anti-cloaking capabilities GeoEdge’s security researchers were able to identify and block the Hermexx attack.
Client-Side vs Server-Side Cloaking
Server-Side
- Mostly rely on the network headers and client IP
- The server filters the requests by comparing the IP and network header to a list of non-targeted locations and devices.
- If there is a client-side – investigate the data sent by the client.
Client-Side
- Mostly used to fingerprint the client device and environment
- And send the data to the server, where it will decide whether this is a targeted user or not.
As explained in the Morphixx attack, as part of every malvertising campaign, the attacker needs to implement the fingerprinting process to avoid detection mechanisms. Cloakers use a client-side script to fingerprint the client device and environment so they can filter non-targeted users like detection engines and security researchers.
In the world of programmatic ads, ad cloaking is a sophisticated camouflage mechanism for malvertisers.
When scammers identify screening efforts, they hide their malicious activity, so if a security tool scans the ad tag, it will not be able to spot malicious activity. Cloaked attacks are expressly designed to pass through a scan at the ad tag level, before the impression is rendered, and to show scanning tech a false result.
Hermexx Attack Breakdown
With campaigns mostly coming from Google AdSense / AdX.The deception starts with a basic but sinister banner:

Which leads non-targeted users to a basic (cloaked) web page:

Although when a targeted user clicks, they will be redirected to a deceptive website with only one purpose: to make the user click on something.
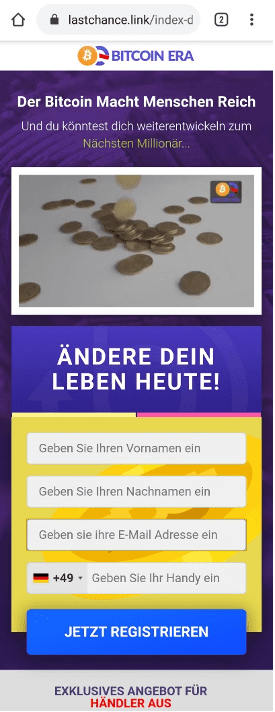
 Once the user clicks, they are redirected to a bitcoin scam
Once the user clicks, they are redirected to a bitcoin scam
Deep Code Analysis
Below is an example of the first stage of client-side cloaking
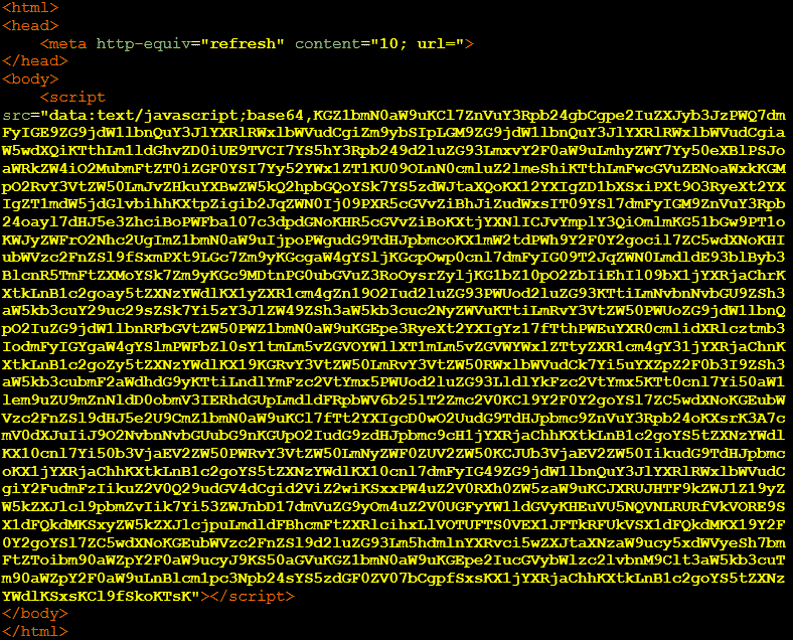
The attacker has encoded his script with base64 encoding to avoid detection engines.
Once removing the encoding, we can see some interesting fingerprinting methods.
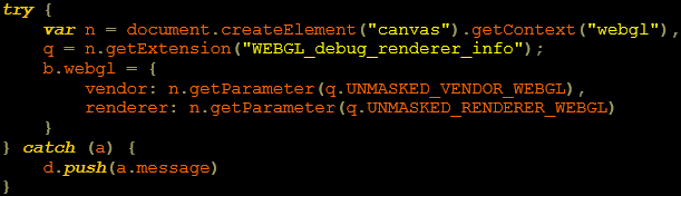
One of the most common methods of fingerprinting is by the JavaScript API WebGL. By investigating the returned object, the attackers can determine whether this is a real device or not.
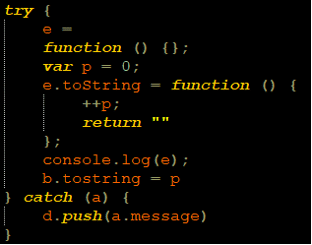
Another fingerprinting method can be seen in the above function. By running the function, the attackers can determine if the browser dev tools is active.
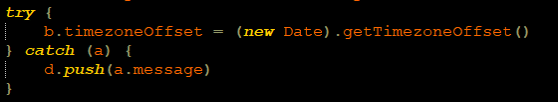
Besides fingerprinting the device itself, the attackers successfully managed to fingerprint the environment by requesting the timezone of the device which will be compared to the timezone of the IP.
Why Cryptocurrency Scams Will Reach New Heights in 2021
2020 was a record year for malicious advertising, with malware attack ads increasing by 85% at the onset of the pandemic. As these numbers attest, cryptocurrency scams geared at credit card fraud have become big business.
This has enticed multinational cybercriminal organizations to invest resources to develop and implement digital advertising-based scams. And the increasing interest in blockchain and cryptocurrency will undoubtedly be met with a significant increase in global malvertising attacks as we start the new year.
While many cloakers slip under the radar thanks to inadequate tech, GeoEdge’s holistic approach identifies cloakers and verifies that sites and apps offer a clean and safe environment.
Staying One-Step Ahead of Cloakers
GeoEdge equips and protects the programmatic ecosystem with multiple detection engines that examine the underlying code of the ad. Our unique machine learning algorithm is comprised of a dozen mechanisms including de-obfuscation, and anti-cloaking capabilities which analyze code through both the cyber and social engineering perspective.
According to Liran Lavi, Head of Security at GeoEdge, “The only way to block increasingly sophisticated and payment-based malicious ad attacks like Hermexx is through continuous and real-time advanced malware detection utilizing patented behavioral code technology,”
GeoEdge’s post-click malware protection guards users against all compromised URLs along the delivery path. Overlaying multiple layers of precision detection, GeoEdge identifies the techniques and identity of attackers across attack vectors ranging from malware, clickbait, and other threats to user experience to detect and block attacks.
Questions about Hermexx?











